let's do it's.
first step
before exploit we must turn off the 'linux ASLR'
i try to see ASLR.
type : cat /proc/sys/kernel/randomize_va_space
in this randomize_va_space i have 0 integer. becouse i have this can be done by passing an integer. if you get 2 when your cat /proc/sys/kernel/randomize_va_space, it's mean we must passing an integer. type echo 0 > /proc/sys/kernel/randomize_va_space enter than type cat /proc/sys/kernel/randomize_va_space and enter.
second step
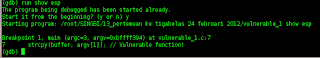
compile our vulnerable application :
// I am a vulnerable thing.
#include <stdio.h>
#include <string.h>
int main(int argc, char** argv)
{
char buffer[500];
strcpy(buffer, argv[1]); // Vulnerable function!
return 0;
}
#include <stdio.h>
#include <string.h>
int main(int argc, char** argv)
{
char buffer[500];
strcpy(buffer, argv[1]); // Vulnerable function!
return 0;
}
than save it.
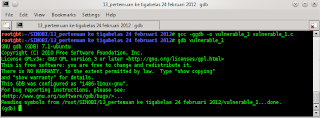
than compile vulnerable code.
than now try to turn the SSP off by adding the “-fno-stack-protector” flag to gcc when compiling.
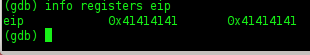
we can see EIP was overflow.
can we see info about register
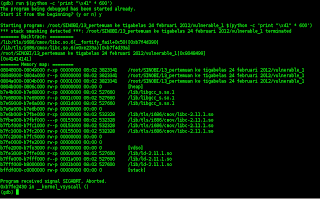
this time we make break on line 7 and try to run ESP, than we can see it's will be break at line 7.
let's see address of ESP than try to run ESP
than now we can check one more again about info ESP
than now we try to genarate payload before that we must have file fore make a payload
after we get payload,
Now that we have all the components let’s try to see how our exploit looks like:
it's still on break than, we must quit than run again.
than see success.
@keep smile & spirit
be fun
than now we try to genarate payload before that we must have file fore make a payload
Now that we have all the components let’s try to see how our exploit looks like:
it's still on break than, we must quit than run again.
than see success.
@keep smile & spirit
be fun









Tidak ada komentar:
Posting Komentar